Straight forward solution
Using the hint provided in the README, extracting the flag is pretty straight forward.
$ strings main32 or main64
A4khf
<flag_here>
It's easy just look harder :)
main.asm
__bss_start
_edata
_end
.symtab
.strtab
.shstrtab
.note.gnu.build-id
.text
.dataNot so striaght forward but cool way
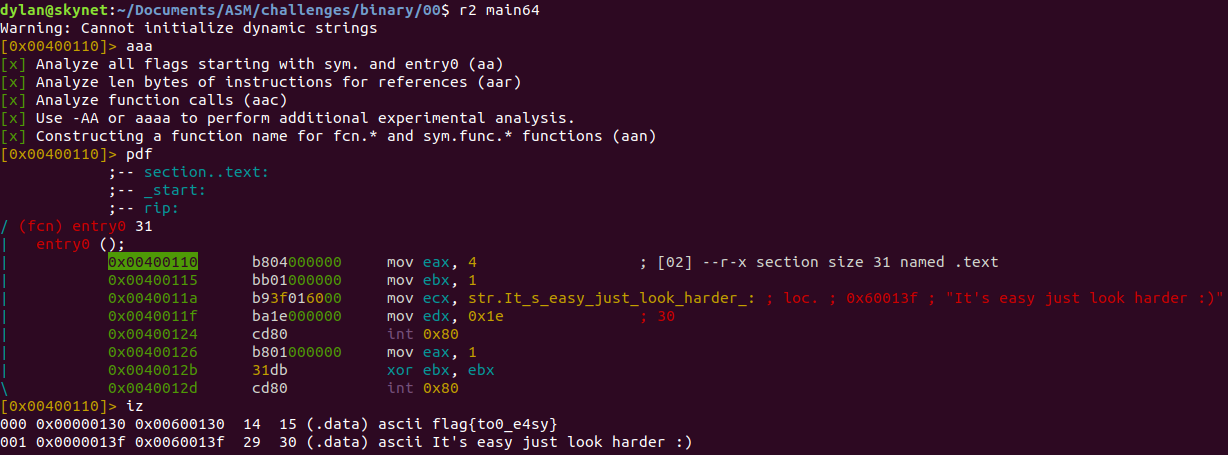
In this method we’ll make use of an awesome tool called radare2 which you can grab from here.
- First open the binary in radare2
$ r2 main32 or main64- Then analyze the binary
[...]> aaa- Disassemble the main function just to check what’s going on.
[...]> pdfNothing interesting over here.
- Now print the strings
[...]> izAnd there you have it.